Pivot for IT and Security
Reduce risk from day one
Involve IT and Security early, so requirements are enforced, compliance is clear, and every vendor decision is secure.
.webp)
Pivot to Pivot
Here's why.
Engage stakeholders early
Involve the right people early to make sure vendor requirements are clear and duplicate requests are caught before they happen.
Keep one source of truth
One place for vendor data, security certifications, and compliance documents so your team meets internal requirements.
Streamline risk assessments
Embed security and compliance checks into procurement workflows to keep reviews consistent, efficient, and on schedule.
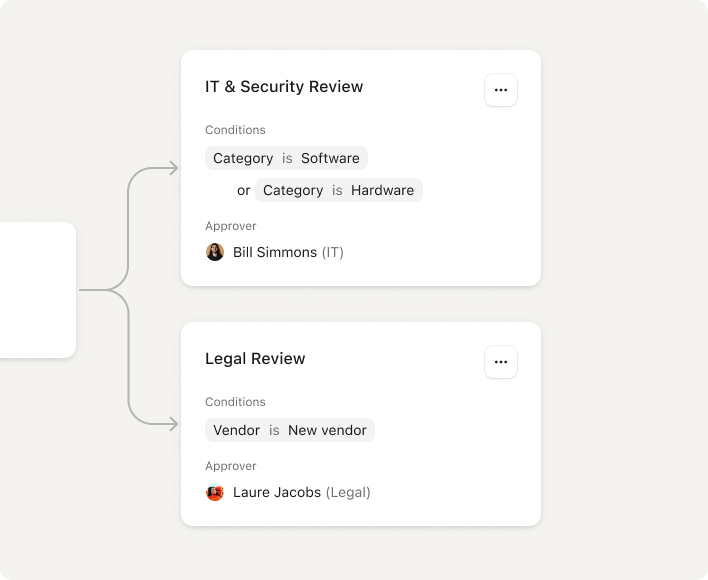
Risk reduction embedded in your processes
Involve IT and Security early, so requirements are enforced, compliance is clear, and every vendor decision is secure.
Involve IT & Security at the right time
Keep your teams in the loop from the very first purchase request so security risks get flagged early, before any contracts are signed.
Explore Approval Workflows
Quick and easy risk assessment
Increase your risk visibility and control to proactively manage vendor threats and safeguard your business.
Explore Vendor Risk Assessment
Natively integrated with your stack
Mask the complexity of mastering multiple tools with Pivot’s native integrations and open API, built to match your unique organizational needs.
Explore Pivot’s Integrations
Your security is our priority
Pivot adheres to SOC 1 Type II, SOC 2 Type II, GDPR, and ISO 27001, keeping your data and privacy safe so you maintain internal control over external compliance.
Explore Pivot’s Security

Risk reduction embedded in your processes
Involve IT and Security early, so requirements are enforced, compliance is clear, and every vendor decision is secure.
Involve IT & Security at the right time
Keep your teams in the loop from the very first purchase request so security risks get flagged early, before any contracts are signed.
Explore Approval Workflows

Quick and easy risk assessment
Increase your risk visibility and control to proactively manage vendor threats and safeguard your business.
Explore Vendor Risk Assessment

Natively integrated with your stack
Mask the complexity of mastering multiple tools with Pivot’s native integrations and open API, built to match your unique organizational needs.
Explore Pivot’s Integrations

Your security is our priority
Pivot adheres to SOC 1 Type II, SOC 2 Type II, GDPR, and ISO 27001, keeping your data and privacy safe so you maintain internal control over external compliance.
Explore Pivot’s Security



.svg)
.svg)
.png)
.png)



.svg)
.svg)
.png)
.png)

.svg)




.png)

.svg)




.png)
Power up with integrations
No-code integrations that help you make life easier for your team.
Discover all integrations
.webp)
Get the support your team needs
A diverse, multilingual team ready to support finance teams across the globe.
Discover the team
Frequently asked questions
What is a Source-to-Pay?
Source-to-Pay (S2P) is a comprehensive procurement process that covers all activities from identifying the need for goods or services through sourcing, contracting, ordering, receiving, and making the final payment to suppliers. It integrates and digitalizes procurement steps into one streamlined workflow to optimize visibility, control, and efficiency across the entire spend lifecycle.
Why implement a source-to-pay solution?
Implementing S2P streamlines procurement, automates workflows, ensures compliance, improves supplier collaboration, and speeds up contract and payment cycles, helping you control spend and make smarter buying decisions.
What's the difference between S2P and P2P?
Source-to-Pay (S2P) covers the entire process from finding and onboarding suppliers, through contract management, right down to purchasing and payment. Procure-to-Pay (P2P) skips the sourcing and contracts part and focuses on the operational flow: creating orders, receiving goods or services, and making payments. Simply put, S2P is broader and starts earlier; P2P handles the buying and paying once suppliers are already chosen.
How does Pivot handle security and compliance?
Pivot uses enterprise-grade security with encryption, role-based access, and compliance with AICPA SOC 1 Type II, AICPA SOC 2 Type II, ISO 27001, and GDPR. Vendor onboarding can include built-in compliance checks.
Which security certifications does Pivot have?
Pivot is certified with SOC 1 Type II and SOC 2 Type II, confirming that its controls for financial reporting, data security, availability, confidentiality, and privacy meet strict industry standards. The company also complies with GDPR, protecting personal data and user privacy across the EU. These certifications and regulations demonstrate Pivot’s focus on data protection, regulatory compliance, and maintaining customer trust.
Procurement Built to Scale Profits,
Not Problems.
Don’t take our word for it. You ask, we answer.
See for yourself inside Pivot.
.svg)

.webp)



.svg)
.webp)
